Now more than ever, FedRAMP certification will put your cloud services or SaaS solution head and shoulders above the competition.
The Federal Risk and Authorization Management Program, or FedRAMP, was designed to support the federal government’s “cloud-first” initiative by making it easier for federal agencies to contract with vendors that provide SaaS solutions and other cloud services. Unlike FISMA, which requires service providers to seek an Authority to Operate (ATO) from each individual agency they want to do business with, a FedRAMP ATO qualifies a provider to work with any federal agency.
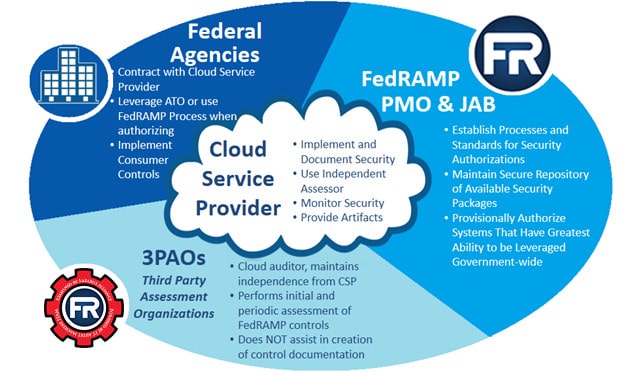
Cloud service providers aren’t required to comply with FedRAMP unless they work with the U.S. federal government. However, FedRAMP certification is a sound investment for all SaaS and cloud services providers, even if they are not currently federal contractors.
FedRAMP will make your company stand out in an increasingly crowded marketplace and reduce your company’s risk exposure
Cloud services and SaaS solutions have exploded in popularity. Everyone is racing to get their piece of the cloud market, and it can be challenging for your solution to stand out, especially if you run a small or mid-sized company. At the same time, consumer anger over data breaches has reached a boiling point, and enterprises are highly concerned about cyber risks, especially risks posed by third-party cloud services and SaaS providers.
Private-sector companies view FedRAMP as a gold standard of data security because they know how companies must meet exacting requirements to obtain it. The FedRAMP certification process will uncover your risks and vulnerabilities, providing a solid foundation for risk assessment, documentation review, and consistent use of internal security protocols that will benefit both your company and your customers.
Completing the FedRAMP certification process will make complying with other standards easier
FedRAMP controls are based on NIST 800-53, which is the basis for other common security regulations and industry standards that your company may have to comply with, including HIPAA, DFARS, PCI DSS, COBIT, ISO 27001, and CJIS.
FedRAMP certification will make it easier for you to sell services to federal contractors
Depending on the services provided, companies that are subcontractors to federal contractors don’t necessarily need to be FedRAMP compliant, but a FedRAMP certification will make your business stand out in this type of scenario as well, especially in this threat environment. The military and other federal government agencies are under attack from nation-state cyber criminals, and in many cases, these hackers target federal contractors and subcontractors. Chinese hackers have already breached U.S. Navy contractors on multiple occasions.
You’ll also have the option of selling services directly to federal government agencies
Federal contracting is stable and lucrative. The U.S. government is the single largest buyer of goods and services in the world, and federal agencies are reliable, steady customers even during economic downturns, when private-sector firms cut back. It’s a particularly attractive market for SaaS developers and other cloud services providers because federal agencies are mandated to be “cloud-first.” A White House directive requires them to evaluate cloud options “before making any new investments.”
Cloud service providers that are FedRAMP certified are listed in the FedRAMP marketplace, so that federal agencies can easily find them when they are looking to buy services.
Become FedRAMP certified at a price you can afford
Enterprises cannot self-certify. FedRAMP certification must be performed by a certified third-party assessment organization (3PAO) such as Lazarus Alliance.
According to FedRAMP.gov, the total median cost for a mid-range cloud services provider to attain a FedRAMP certification is $2,250,000. About half of this is for engineering costs, with the other half spent on the process itself. Additionally, providers can expect to spend about $1,000,000 a year on continuous monitoring to maintain an acceptable risk posture.
Lazarus Alliance understands that these costs are out of reach for most small and medium-sized providers, and we think that’s a shame. Our industry-leading FedRAMP 3PAO services will enable you to expand your business into government markets at a price you can afford. We work smarter, not harder, to drive down your costs by giving you access to Continuum GRC’s proprietary IT Audit Machine (ITAM), the number-one ranked FedRAMP-ready SaaS GRC audit software solution. ITAM utilizes pre-loaded, drag-and-drop modules to simplify and accelerate the FedRAMP certification process. Some of our clients have saved up to 1,000% over traditional FedRAMP assessment methods.
The cybersecurity experts at Lazarus Alliance have deep knowledge of the cybersecurity field, are continually monitoring the latest information security threats, and are committed to protecting organizations of all sizes from security breaches. Our full-service risk assessment services and Continuum GRC RegTech software will help protect your organization from data breaches, ransomware attacks, and other cyber threats.
Lazarus Alliance is proactive cybersecurity®. Call 1-888-896-7580 to discuss your organization’s cybersecurity needs and find out how we can help your organization adhere to cybersecurity regulations, maintain compliance, and secure your systems.




