HBO Hacks Indicate a Company in Cyber Security Crisis
Hacks in the City: Latest in String of HBO Hacks Targets Company’s Social Media Accounts
HBO has had a rough summer, and things are getting progressively worse for the cable titan. The HBO hacks began in late June, when an individual hacker or group calling themselves “Mr. Smith” dumped several episodes of upcoming HBO series and the script to an upcoming Game of Thrones episode online. Mr. Smith claimed to have stolen approximately 1.5TB of data and threatened to release all of it unless HBO paid them $6 to $7 million. HBO countered with an offer of $250,000. Mr. Smith apparently found this laughable and continued to leak not only content and scripts but confidential emails and the personal data of the GoT cast.

While the attention of the media (and HBO) was focused on Mr. Smith, a full upcoming episode of GoT was released online. This wasn’t the work of Mr. Smith but that of malicious insiders at a company called Prime Focus Technologies, a third-party vendor of Star India, HBO’s business associate that airs GoT in India. In other words, HBO was victimized by a hack at a third-party vendor of a third-party vendor.
In Incident #3 in the string of HBO hacks, the company “hacked” itself. This time, an apparent employee mistake at HBO Nordic and HBO España, two European affiliates of HBO, resulted in the first hour of an episode of GoT being aired four days early. It didn’t take long for the content to appear online.
The network’s latest Excederin headache came on last week, when a separate hacker or group calling itself OurMine, which was behind several high-profile social media takeovers at other companies, took control of HBO’s Twitter and Facebook accounts.
It is highly unlikely the HBO hacks will stop anytime soon. Around the same time as the OurMine social media debacle, Mr. Smith contacted Mashable and sent them “what appears to be the login credentials for almost every single HBO social media account. Passwords for everything from @HBO, @GameOfThrones, and @WestworldHBO to various Instagram and Giphy accounts.” Mr. Smith also claimed to be in possession of the season finale of GoT and solemnly vowed to release it if HBO didn’t pay up soon.
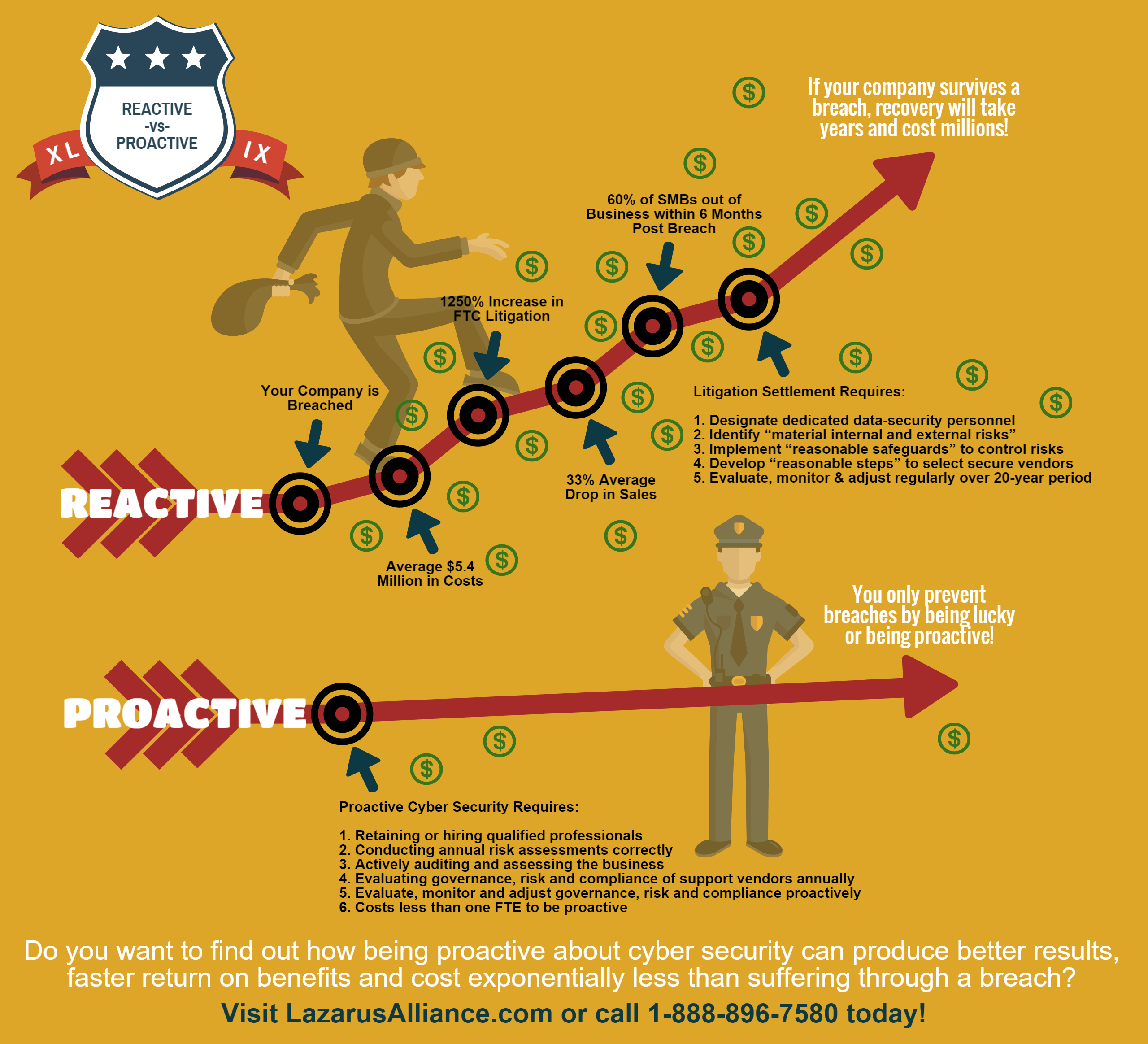
Hey HBO, how’s that reactive cyber security working out for you?
The HBO hacks involve multiple cyber security issues, including malicious insiders, innocent but damaging employee errors, third-party vendor hacks, email hacks, corporate espionage, theft of digital IP and company secrets, and login credentials theft – and that’s just what’s happened and what we know about so far. It hasn’t yet been determined exactly how Mr. Smith and OurMine got hold of the credentials they needed to breach HBO’s internal network and social media accounts, but usually, login credential theft occurs through email phishing scams, so we’re probably looking at more employee error.
Two things are clear: HBO is a company in cyber security crisis, and it has inadvertently become a case study of why reactive cyber security doesn’t work. The fact that is being attacked on multiple fronts, by multiple parties, is indicative of a longstanding reactive stance to cyber attacks and deep-rooted security vulnerabilities at all levels of the organization. It desperately needs to implement sound GRC and proactive cyber security practices and wrest back control over its entire enterprise cyber ecosystem.
How much will all of this end up costing HBO in the end? Whatever the final number is, it’s safe to bet that it would have been a lot cheaper and far less damaging if HBO had never lost control over its cyber security in the first place.
The cyber security experts at Lazarus Alliance have deep knowledge of the cyber security field, are continually monitoring the latest information security threats, and are committed to protecting organizations of all sizes from security breaches. Our full-service risk assessment services and Continuum GRC RegTech software will help protect your organization from data breaches, ransomware attacks, and other cyber threats.
Lazarus Alliance is proactive cyber security®. Call 1-888-896-7580 to discuss your organization’s cyber security needs and find out how we can help your organization adhere to cyber security regulations, maintain compliance, and secure your systems.