Artificial Intelligence in Cybersecurity
Artificial Intelligence (AI) can be used in the Cybersecurity Industry in many ways, which are still yet to be tapped into. Just as much as other technologies are constantly and dynamically changing, so too is this field. It has just started to make its debut for security applications, and there is a long way to go yet until it is fully adopted and deployed.
But Artificial Intelligence is being used in some key areas in Cybersecurity, which are as follows:
- Many Cyberattacks are starting to go unnoticed today. There are two primary reasons for this:
-
- The IT Security team is so overworked that they are simply, through no fault of their own, are letting the real threat warnings and alerts fall through the cracks;
- The Cyberattacker is becoming so sophisticated that many of the threat vectors that they do launch are very often not detected by the security tools that have been deployed at the lines of defenses.

Through the use of Artificial Intelligence tools, many of these kinds of attacks are now starting to get noticed, and by establishing a threshold of interoperability with other devices (such as Network Intrusion Devices, Firewalls, Routers, etc.) these kinds of threat vectors are now getting stopped in their tracks even before they make an entry into the IT and Network Infrastructure of an organization.
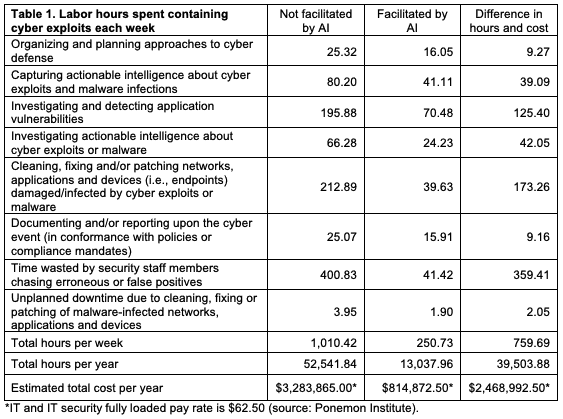
- The severe shortage of skilled workers in the Cybersecurity Industry has left a huge void that needs to be filled by the existing employees in the workplace. Thus, this is adding on an even extra layer of burden and workload, especially when it comes to conducting routine and daily tasks. In this aspect, Artificial Intelligence can automate these kinds of job functions, thus allowing the IT Security staff to focus in on the more crucial areas of their job functions. Another added benefit is that depending upon the tool that is being used, many Artificial Intelligence systems of today do not require any sort of human intervention. This simply means that once they have been programmed to any certain kinds of tasks, the reliability of them to deliver a high-quality product is quite robust. The graphic below clearly demonstrates how the use of Artificial Intelligence can help augment an IT Security staff, based upon the number of labor hours that can be saved by automating the following tasks:

- In Cybersecurity today, one of the hot topics that is coming about is that of Multi Factor Authentication, or “MFA” for short. This is where more than one layer of defense is used in order to protect IT and Network Assets. For example, rather than just a using a password to gain access to shared resources, there are other authentication mechanisms that an individual will have to go through in order to positively confirm their identity. This could include incorporating the usage of Challenge/Response Questions, RSA Tokens, Smart Cards, Biometrics, etc. While all of these are very reliable means of authentication when they are used in conjunction with another, there is still fear that a Cyberattacker can still break through any of these. Thus, there is very serious consideration being given to using Artificial Intelligence as yet another layer of authentication. But the difference here is that these kinds of systems can actually build a profile of the end user and allow for authentication based upon th t person’s predictive behavior. In other words, Artificial Intelligence can make a holistic judgement (based upon an infinite number of variables) in real time if the end user is really claiming with 100% authenticity whom they are to be.
- At the present time, Artificial Intelligence is being used to aid in the protection of certain aspects of the IT and Network Infrastructure, from both a hardware and software application standpoint. In other words, it is only being used in local instances, not at an enterprise level, which will encompass the entire organization. It is highly anticipated, by the way that the AI technology is rapidly advancing, that this particular level of protection will become a reality in the short term.
- One of the oldest and still most widely used form of threat vectors that is used is that of Phishing. There are many new variants of it that are coming out today, especially in the way of Business Email Compromise (also known as “BEC”) and Ransomware. Once again, there are so many of these that are rampant today that it is close to impossible for an IT Security staff to keep up with all of this. For example, it has been cited that 1 out of every 99 Email messages is a Phishing based one. While that may not seem like a lot, just think about the total number of messages that are sent in one day from just one business. This ratio can multiply at least 100X. An Artificial Intelligence tool can track these notorious Emails much quicker than any human being can at a rate of 10,000 messages at any given moment in time. Another advantage of using Artificial Intelligence there are no geographic limitations in which it can detect for Phishing Emails (it can virtually understand any language if it has been programmed that way), and it can also differentiate between a spoofed website and an authentic one in just a matter of seconds.
The Functionalities, or Characteristics Of An Artificial Intelligence System In Cybersecurity
As it relates to Cybersecurity, there are three main functionalities of an Artificial Intelligence system which makes it very different from the other security tools that are available.
They are as follows:
- It can learn:One of the main themes that has been pointed is that a good AI system can learn, with or without human intervention (of course, the latter is much more preferred). The way that it learns is that literally billions of pieces of data are fed into it, via many intelligence feeds. Once this data is fed into it, the Artificial Intelligence tool can then “learn” from it by unearthing any trends or threat vector-based attack signatures that have not been discovered previously. It can even also learn from known trends as well. By combining these two together, the AI system can then make reasonably accurate observations or predictions as to what the Cyber Threat Landscape will look like on a daily basis, if that it is what the main purpose of has been designed to accomplish. It is important to note, while this is done on a 24 X 7 X 365 basis, the data and information that is fed into it must be done on an almost minute by minute basis. If this is not done, the AI system can lose its robustness very quickly, can literally become “stale”. Also, based upon the datasets that are fed into it, a good AI system can also even make recommendations to the IT Security team as to what the best course of action it can take in just a matter of minutes. In this regard, Artificial Intelligence can also be used as a vehicle for threat mitigation by the Cyber Incident Response Team. An AI system that is designed for the Cybersecurity Industry can also digest, analyze, and learn from both structured and unstructured datasets (this even includes the analysis of written content, such as blogs, news articles, etc.).
- It can reason:Unlike the other traditional security technologies, Artificial Intelligence tools can also reason and even make unbiased decisions based upon the information and data that is fed into it. In other words, an AI system can look at multiple threat vectors all at once and take notice of any correlations that may exist between them. From this, a profile of the Cyberattacker can be created and even used to prevent other new threat variants from penetrating into the lines of defenses. Very often, a Cyberattacker will launch differing attacks so that they can evade detection. For example, Cyberattackers have been known to hide their tracks after penetrating an IT/Network Infrastructure by covertly editing the system logs of the servers, or even just simply reset the modification date on a file that has been hijacked but replaced with a phony file. These cannot be detected by the standard Intrusion Detection Systems (IDSs) that are being used today; they can only be discovered by anomalies if significant deviations can be found. But with the use of AI, these and other hidden commonalities can be discovered very quickly in order to track down the very elusive Cyberattacker. Also, an AI system does not take a “Garbage In/Garbage Out” view of a threat vector. It tries to make logical hypotheses based upon what it has learned in the past. In fact, it has been claimed that Artificial Intelligence can respond to a new threat variant 60X faster than a human could ever possibly do.
- It can augment:Again, as it has been mentioned before in the last subsection, one of the biggest advantages of Artificial Intelligence in Cybersecurity is that it can augment existing resources. Whether it is from filling the void from the lack of the labor shortage, or simply automating routine tasks that need to be done, or even filtering through all the false positive warnings and messages to determine which of those are for real, AI can absorb all of these time consuming functions that can take an IT Security team hours to accomplish and get them done in just a matter of minutes. It can also be a great tool to conduct tedious research-based tasks, can calculate the levels of risk very quickly so that the IT Security team can respond to a Cyber Threat in just a matter of seconds and mitigate it quickly.
Conclusions
It is important to keep in mind that AI is still taking its roots in Cybersecurity, and there are many areas that it could potentially be used for. Future blogs will examine greater detail these applications.
The cybersecurity experts at Lazarus Alliance have deep knowledge of the cybersecurity field, are continually monitoring the latest information security threats, and are committed to protecting organizations of all sizes from security breaches. Our full-service vulnerability testing services will help protect your organization from data breaches, ransomware attacks, and other cyber threats.
Lazarus Alliance is proactive cybersecurity®. Call 1-888-896-7580 to discuss your organization’s cybersecurity needs and find out how we can help your organization adhere to cybersecurity regulations, maintain compliance, and secure your systems.




Related Posts