C5 Audit and Assessments; we are ready when you are! Call +1 (888) 896-7580 today.
Table of Contents
Toggle
Lazarus Alliance will work closely with your organization to arrange and conduct a Cloud Computing Compliance Controls Catalog (C5) assessment tailored to your needs. Our experienced assessors will collaborate with you to evaluate your company’s specific business requirements and determine the appropriate C5 certification level that aligns with your operational and security maturity. Upon successful demonstration of the required capabilities and organizational maturity, your company will be awarded C5 certification at the corresponding level.
The C5 framework, established by Germany’s Federal Office for Information Security (BSI), is a government-backed attestation scheme designed to ensure organizations meet robust operational security standards to protect against common cyber threats. It is rooted in the German Government’s "Security Recommendations for Cloud Providers," providing a structured approach to assess and validate the security and compliance of cloud-based services. This certification helps organizations demonstrate their commitment to maintaining high security standards, enhancing trust with clients and stakeholders in the context of cloud computing.
Cloud Computing Compliance Controls Catalog (C5)
C5, or the Cloud Computing Compliance Criteria Catalogue, is a security standard developed by Germany's Federal Office for Information Security (BSI) to ensure robust cloud computing practices. It provides a comprehensive set of audited controls covering 17 key areas, including organizational measures, data protection, access controls, and incident management, drawing from frameworks like ISO 27001, ISO 27017, and the Cloud Security Alliance's Cloud Control Matrix. Audits are conducted under ISAE 3000 standards, resulting in an attestation (Type 1 for design or Type 2 for design and effectiveness) that verifies the cloud provider's internal control system. The latest version, C5:2025, includes updates like enhanced criteria for container management, supply chain security, and post-quantum cryptography. Audits can be combined with others (e.g., SOC 2) for efficiency and must be performed by qualified independent auditors, with re-audits typically every 6-12 months.
C5 Applies To:
- Public entities: All public administration bodies, including central, regional, and local government organizations, to secure their electronic services and data.
- Private entities: Organizations providing services to public administrations or handling sensitive data linked to public services, such as critical infrastructure providers or contractors.
C5 primarily applies to cloud service providers (CSPs) offering IaaS, PaaS, or SaaS solutions, especially those serving or targeting the German market, to demonstrate compliance with baseline security requirements. It is mandatory for federal government agencies in Germany to procure external cloud services and recommended, but increasingly expected for private organizations, including those handling sensitive data under GDPR or working with government entities. Customers use C5 reports to evaluate providers, while subcontractors in cloud chains may also need to comply.
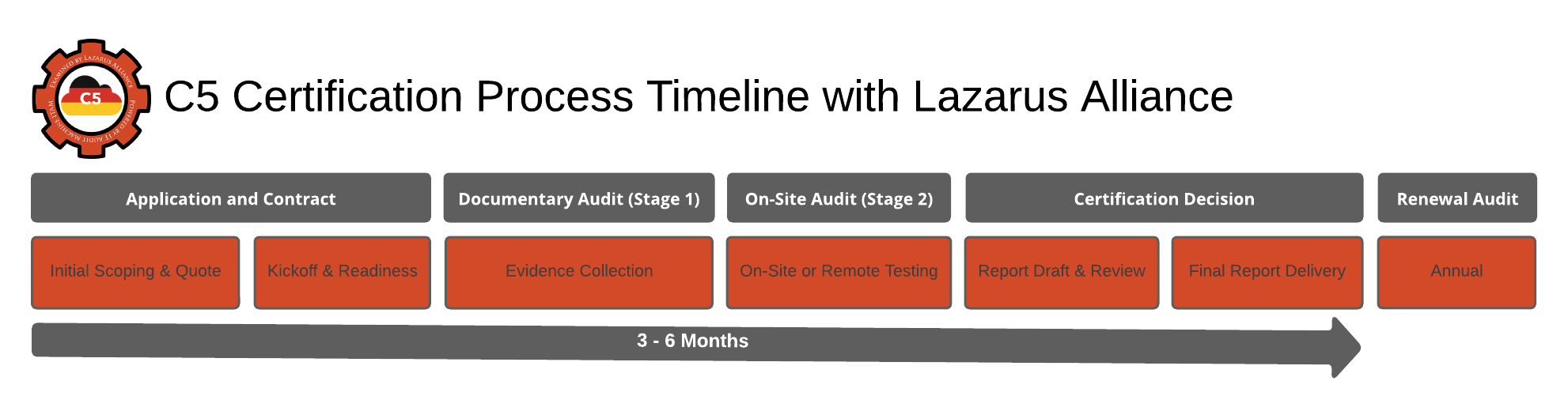
C5 Certification Audit Timeline with Lazarus Alliance
Achieving C5 certification through Lazarus Alliance's audit services provides cloud service providers (CSPs) with a structured path to compliance under the BSI's Cloud Computing Compliance Controls Catalog. The process is designed to be efficient, typically spanning 3-6 months from initial scoping to final attestation, depending on your organization's readiness, the complexity of your cloud environment, and whether you're pursuing a Type 1 or Type 2 audit. This timeline incorporates preparation, execution, remediation, and reporting, with Lazarus Alliance's experienced Cybervisor™ teams guiding you every step to minimize disruptions.
Factors influencing the timeline include:
- Organizational Maturity: Well-prepared CSPs with existing controls (e.g., aligned to ISO 27001) can complete in closer to 3 months.
- Scope: Including subcontractors or multi-region operations may extend it to 6 months.
- Audit Type: Type 1 is faster (point-in-time focus), while Type 2 requires 6-12 months of operational evidence collection.
- Remediation Needs: Major non-conformities must be resolved before attestation, potentially adding 1-2 months.
- Integrations: Bundling with SOC 2 or other audits can shorten overall efforts by leveraging overlaps.
Re-certification requires re-audits every 6-12 months to maintain validity, with ongoing monitoring to address updates like C5:2025 enhancements (e.g., supply chain security).
Detailed Timeline Phases
The process unfolds in five key phases, as outlined below. Lazarus Alliance collaborates closely to tailor the approach, ensuring compliance across C5's 17 domains (e.g., access controls, incident management).
| Phase | Description | Estimated Duration | Key Activities with Lazarus Alliance |
|---|---|---|---|
| 1. Preparation & Scoping | Define audit boundaries, including services, systems, and subcontractors. Conduct gap analysis against C5 criteria. | 2-4 weeks | - Initial consultation to assess maturity. - Gap analysis using tools aligned with ISO 27001/Cloud Control Matrix. - Select ISAE 3000-accredited auditors from our network. |
| 2. Documentation & Evidence Collection | Gather policies, procedures, configurations, and proof of controls. Map to C5's 17 areas. | 4-8 weeks (overlaps with Phase 1) | - Collaborative evidence review sessions. - Support for aligning docs with global standards. - Early identification of gaps to accelerate remediation. |
| 3. Audit Execution | On-site/remote assessments, interviews, and control testing. Covers design (Type 1) or effectiveness (Type 2). | 4-6 weeks | - Led by Cybervisor™ experts for thorough, risk-based evaluations. - Includes subcontractor audits if scoped. - Real-time feedback to address issues promptly. |
| 4. Reporting & Attestation | Review draft report, remediate findings, and issue final attestation. | 2-4 weeks | - Detailed findings report with remediation guidance. - Assistance in resolving non-conformities. - Final ISAE 3000-compliant report for stakeholders. |
| 5. Ongoing Maintenance | Implement continuous monitoring and prepare for re-audits. | Post-certification (ongoing; re-audit every 6-12 months) | - Advisory on C5:2025 updates (e.g., post-quantum crypto). - Annual health checks to ensure sustained compliance. |
Type 1 vs. Type 2 Timeline Comparison
- Type 1 (Design-Focused): Emphasizes control suitability at a snapshot in time. Total timeline: 3-4 months. Ideal for initial certifications or proving foundational security.
- Type 2 (Operational Effectiveness): Builds on Type 1 with 6-12 months of performance evidence. Total timeline: 4-6 months (plus evidence period). Provides stronger assurance for regulated clients, like German government contracts.
Next Steps
Contact Lazarus Alliance today to kick off your C5 journey—our team can provide a customized timeline estimate based on a free initial scoping call. This certification not only unlocks EU market opportunities but also bolsters your security posture against evolving threats.
Frequently Asked Questions
What is C5?
C5, or the Cloud Computing Compliance Controls Catalog, is a security standard developed by Germany's Federal Office for Information Security (BSI). It provides a comprehensive set of audited controls across 17 key areas, such as organizational measures, data protection, access controls, and incident management. Rooted in the German Government’s "Security Recommendations for Cloud Providers," it draws from frameworks like ISO 27001, ISO 27017, and the Cloud Security Alliance's Cloud Control Matrix. Audits are conducted under ISAE 3000 standards, resulting in Type 1 (design) or Type 2 (design and effectiveness) attestations.
Why is C5 compliance important for organizations?
C5 compliance ensures robust operational security against cyber threats in cloud environments, enhances trust with clients and stakeholders, and aligns with international best practices like GDPR. It reduces risks of data breaches and disruptions, provides a competitive edge in regulated markets, and streamlines customer due diligence through standardized reports. For organizations targeting Germany or the EU, it's essential to access government contracts and demonstrate high security standards.
Who needs a C5 audit?
C5 is primarily for cloud service providers (CSPs) offering IaaS, PaaS, or SaaS solutions, especially those serving the German market. It's mandatory for providers working with German federal government agencies and recommended for private organizations handling sensitive data under GDPR, critical infrastructure providers, or those in public sector contracts. Subcontractors in cloud supply chains may also require it to maintain consistent security.
What are the benefits of achieving C5 compliance with Lazarus Alliance?
Benefits include enhanced market credibility and trust, access to German government contracts, improved security posture across 17 domains, and alignment with global standards like ISO 27001 and SOC 2. It supports GDPR compliance, mitigates risks (e.g., supply chain security and post-quantum cryptography), and offers cost efficiencies by combining audits. Our Cybervisor™ teams ensure tailored assessments that differentiate you in competitive, regulated industries
What does the C5 audit process involve?
The process typically takes 3-6 months and includes:
- Preparation and scoping (gap analysis and auditor selection).
- Documentation and evidence collection (mapping controls to C5 criteria).
- Audit execution (Type 1 or Type 2 assessments via on-site/remote reviews, interviews, and tests).
- Reporting and attestation (remediating findings and issuing the final report).
- Ongoing maintenance (re-audits every 6-12 months). Lazarus Alliance handles this collaboratively, incorporating C5:2025 updates for efficiency.
How does Lazarus Alliance conduct C5 audits?
We partner closely with your team to evaluate business needs and maturity, using experienced Cybervisor™ assessors accredited under ISAE 3000. Audits cover risk-based controls in 17 domains, with options for Type 1 or Type 2 levels, and can integrate with other standards like SOC 2. We perform assessments worldwide, including subcontractor evaluations, and provide tailored support for remediation. Clients supply documentation, access, and incident records for a smooth process.
How can organizations prepare for a C5 audit?
Start with an internal gap analysis against C5's 17 domains, define scope (including subcontractors), and compile policies, procedures, and evidence. Map controls to C5 criteria using overlaps with ISO 27001 or Cloud Security Alliance frameworks. Engage an accredited auditor early, address non-conformities promptly, and maintain records of incidents and changes. Lazarus Alliance recommends combining preparations with other audits to save time and resources.
What are the differences between C5 Type 1 and Type 2 attestations?
Type 1 focuses on the design and implementation of controls at a specific point in time, verifying if they're suitably designed to meet C5 criteria. Type 2 goes further, assessing both design and operational effectiveness over a 6-12 month period through testing. Type 2 provides stronger assurance for stakeholders but requires more preparation. Lazarus Alliance can guide you on selecting the right level based on your goals and maturity.

Benefits of C5 Compliance
C5 (Cloud Computing Compliance Criteria Catalogue) compliance offers several advantages for cloud service providers (CSPs), their customers, and organizations operating in or targeting the German market. Below is a concise overview of the key benefits:
- Enhanced Trust and Market Credibility C5 compliance demonstrates a CSP’s commitment to robust security and data protection standards, building trust with customers, particularly German federal agencies and private organizations handling sensitive data.
- Access to German Government Contracts C5 is mandatory for CSPs serving German federal government agencies, enabling providers to qualify for public sector contracts and expand their market reach.
- Alignment with Global Standards C5 incorporates elements from ISO 27001, ISO 27017, and the Cloud Security Alliance’s Cloud Control Matrix, ensuring alignment with international best practices, which simplifies compliance with other frameworks like GDPR or SOC 2.
- Improved Security Posture The rigorous audit process, covering 17 domains such as access controls, incident management, and supply chain security, strengthens a provider’s overall security framework, reducing vulnerabilities.
- Competitive Advantage Achieving C5 attestation differentiates CSPs in a competitive market, signaling to clients that their services meet high security and compliance standards, especially in regulated industries.
- Streamlined Customer Due Diligence C5 audit reports provide customers with a standardized, transparent evaluation of a provider’s controls, reducing the need for extensive individual assessments and accelerating procurement decisions.
- Support for GDPR Compliance C5’s focus on data protection and privacy aligns with GDPR requirements, helping organizations ensure compliance when processing personal data in the EU.
- Risk Mitigation By addressing areas like post-quantum cryptography and supply chain security (updated in C5:2025), compliance reduces risks related to cyber threats, data breaches, and operational disruptions.
- Cost and Time Efficiency Combining C5 audits with other standards (e.g., SOC 2 or ISO 27001) minimizes redundant efforts, saving time and resources for CSPs pursuing multiple certifications.
- Scalability for Subcontractors C5 compliance extends to subcontractors in the cloud supply chain, ensuring consistent security standards across all partners, which is critical for complex cloud ecosystems.
By achieving C5 compliance, CSPs not only meet regulatory expectations but also position themselves as secure, reliable partners in the cloud services market, particularly in Germany and the broader EU.

Talk with one of our experts
Our Lazarus Alliance Cybervisor™ teams have experience performing thousands of assessments for organizations providing services to clients around the world.
We're here to answer any questions you may have.

C5 Certification Process
The C5 (Cloud Computing Compliance Criteria Catalogue) certification process, developed by Germany's Federal Office for Information Security (BSI), involves a structured approach to assess and validate a cloud service provider’s (CSP) security and compliance controls. Below is a concise overview of the C5 certification process:
- Preparation and Scoping
- Identify Scope: The CSP determines the cloud services, systems, and locations to be audited, ensuring all relevant infrastructure, processes, and subcontractors are included.
- Gap Analysis: Conduct an internal review to assess current controls against C5’s 17 domains (e.g., access control, data protection, incident management). Identify gaps and implement necessary improvements.
- Select Auditor: Engage a qualified independent auditor accredited under ISAE 3000 standards to perform the audit.
- Documentation and Evidence Collection
- Compile Documentation: Gather policies, procedures, technical configurations, and evidence demonstrating compliance with C5 requirements, including organizational measures, supply chain security, and updates like post-quantum cryptography (C5:2025).
- Control Mapping: Align internal controls with C5 criteria, often referencing related standards like ISO 27001 or Cloud Security Alliance’s Cloud Control Matrix.
- Audit Execution
- Type 1 or Type 2 Audit:
- Type 1: Evaluates the design and implementation of controls at a specific point in time (snapshot).
- Type 2: Assesses both design and operational effectiveness over a period (typically 6-12 months), requiring evidence of consistent control performance.
- On-Site and Remote Assessments: The auditor reviews documentation, conducts interviews, and tests controls to verify compliance.
- Subcontractor Evaluation: If applicable, auditors assess subcontractors in the cloud supply chain to ensure consistent security standards.
- Type 1 or Type 2 Audit:
- Audit Report and Attestation
- Draft Report: The auditor issues a draft report detailing findings, including any deficiencies or non-conformities.
- Remediation: The CSP addresses identified issues, if any, to meet C5 requirements.
- Final Attestation: Upon successful audit, the auditor issues a C5 attestation (Type 1 or Type 2), which serves as proof of compliance. The report is shared with customers or regulators as needed.
- Ongoing Maintenance and Re-Audits
- Continuous Monitoring: Maintain compliance by regularly updating controls to align with C5:2025 updates and evolving threats.
- Re-Audits: Conduct follow-up audits every 6-12 months to renew attestation, ensuring ongoing adherence to C5 standards.
- Optional Integration with Other Standards
- CSPs can combine C5 audits with other frameworks (e.g., SOC 2, ISO 27001) to streamline compliance efforts, leveraging overlapping controls to reduce time and cost.
Key Notes
- Applicability: Primarily for CSPs (IaaS, PaaS, SaaS) targeting the German market, especially those serving federal government agencies or private organizations under GDPR.
- Timeframe: The process typically takes 3-6 months, depending on the CSP’s readiness and audit scope.
- Auditor Role: Only ISAE 3000-accredited auditors can issue C5 attestations, ensuring credibility and consistency.
- Outcome: A successful audit results in a C5 attestation, enhancing trust, enabling government contracts, and demonstrating robust security to customers.
For detailed requirements, CSPs can refer to the BSI’s official C5 documentation or consult a qualified auditor.

Additional Notes
- Accreditation Requirements: The auditing body must be accredited under ISAE 3000 standards by a recognized accreditation authority to ensure impartiality and competence, aligning with international auditing standards.
- Client Responsibilities: The cloud service provider (CSP) must provide auditors with access to relevant documentation, personnel, and infrastructure, maintain records of security incidents or complaints, and inform the auditor of significant changes to systems or processes, as required by ISAE 3000 guidelines.
- C5-Specific Considerations: The C5 audit process emphasizes risk-based security controls across 17 domains (e.g., access control, incident management, supply chain security), with enhanced requirements in C5:2025 for areas like post-quantum cryptography and container management. The BSI provides detailed guidance on C5 implementation, which auditors incorporate into the process.
- Non-Conformities: Any non-conformities identified during the audit must be resolved within a timeframe agreed upon with the auditor. Major non-conformities (e.g., critical security vulnerabilities) typically require resolution before attestation is issued, while minor ones may be addressed during follow-up or re-audits.
