On July 16, the social media platform Twitter experienced one if not the most significant, security breaches in its history when cybercriminals hacked into major public figures’ verified accounts and convinced users worldwide to transfer them nearly $120,000 in bitcoin. What can other organizations learn from this Twitter hack?
What was the Twitter Hack?
A mobile spearphishing attack targeting “a small number of employees” led to the unprecedented, major attack in July of 2020 on high-profile Twitter accounts to push out a Bitcoin scam.
“This attack relied on a significant and concerted attempt to mislead certain employees, and exploit human vulnerabilities, to gain access to our internal systems,” the company said in its update. “This was a striking reminder of how important each person on our team is in protecting our service.”
On the day of the attack, Twitter revealed that the accounts fell victim to a compromise of the company’s internal systems by a group of unidentified hackers that managed to access Twitter’s company tools and secure employee privileges.
Since not all of the initially targeted employees had permissions to use the account management tools key to the attack, the attackers used a two-step approach to hack their way in, according to Twitter. They first used the initial credentials they phished to access some of Twitter’s internal systems and learn information about company processes, according to the post.
“This knowledge then enabled them to target additional employees who did have access to our account-support tools,” the company said. “Using the credentials of employees with access to these tools, the attackers targeted 130 Twitter accounts, ultimately tweeting from 45, accessing the DM inbox of 36, and downloading the Twitter Data of seven.”
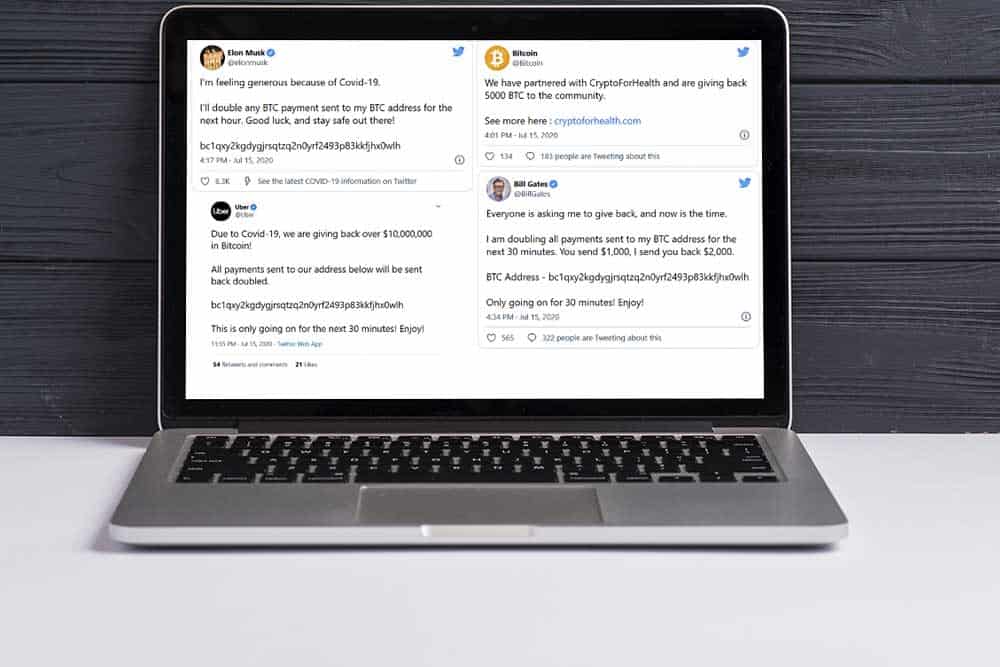
The result…
Twitter saw a hack on an unprecedented scale on Wednesday when scammers targeted multiple high-profile accounts, sending a volley of tweets extorting Bitcoin from the 346 million followers of Barack Obama, Apple, Uber, Joe Biden, Elon Musk, and 20 others.
The tweets promised users that the account holders would double the donations they sent to the Bitcoin addresses provided—a classic scam. The hackers walked away with around $120,000, but, more importantly, they left some critical lessons for social media platforms and the crypto industry in their wake.
The perpetrators of the attack were eventually caught. Florida resident Graham Clark was arrested on Friday, July 31. State Attorney Andrew Warren filed 30 felony charges, including organized fraud, communications fraud, fraudulent use of personal information, and access to computer or electronic devices without authority.
According to criminal complaints published Friday, July 31, federal officials are also charging Nima Fazeli and Mason John Sheppard with aiding in the “intentional access of a protected computer” and conspiracy to commit wire fraud and money laundering.
What is a Spearphishing attack?
Spear phishing is an email or electronic communications scam targeted towards a specific individual, organization, or business. Although often intended to steal data for malicious purposes, cybercriminals may also intend to install malware on a targeted user’s computer.
This is how it works: An email arrives, apparently from a trustworthy source, but instead, it leads the unknowing recipient to a bogus website full of malware. These emails often use smart tactics to get victims’ attention.
Cybersecurity Lessons learned from the Twitter Attack
Insider Threats are dangerous
Too often, employees aren’t aware they could be violating security policies or don’t understand how shortcuts can put customers’ data. Anyone with trusted access to data can exploit vulnerabilities that lead to millions of dollars in damage. In Twitter’s case, the hacker was able to access its internal systems after first gaining entry into Twitter’s Slack account, where, allegedly, he found unspecified Twitter credentials that gave him access to the company’s servers, according to The New York Times.
The attack broke into the Twitter accounts of world leaders, celebrities, and tech moguls, and sent out tweets from those accounts offering to pay the sender double any payment they made to a Bitcoin wallet address. The hackers also reset the passwords of 45 of the 130 accounts targeted.
Data breaches are still too common
Data breaches are nothing new. And breaches are inevitable if you’re in the data business. A lot of the data that companies regularly collect, manage, and store is sensitive data that is vulnerable to a breach and subject to regulations, such as the GDPR or CCPA.
Research estimates that for every production instance of an application, there are typically over ten copies of non-production. Insiders, such as developers, analysts, and testers, often have broad access to these lower environments containing a vast majority of sensitive data to carry out their responsibilities.
Unlike production systems that are highly protected, non-production environments carry more risk and are generally less protected. While hackers and malicious attackers are mostly to blame, organizations can do a better job protecting their data than by inadvertently leaving their sensitive data vulnerable or exposed.
Now is the time to review your Cybersecurity Plan
Despite a worldwide pandemic, hackers are continuing to unleash cyberattacks on businesses. Companies like Nintendo, Estée Lauder, Microsoft, and others have been hit hard by data hacks.
The main takeaway from this most recent incident is that attackers were able to defeat the intrusion detection systems and gain access to production. Why the internal staff had access to live systems and their data is unknown at this time, but this is an essential lesson in the cyber world—employees continue to be the biggest weakness in IT security. There is no justification in the modern world for keeping backdoor access to customer data. Because if there’s a way to do it, malicious actors will exploit it.
Conclusions from the 2020 Twitter Hack
As with all cybersecurity issues, the best defense is a good offense. Lazarus Alliance recommends that organizations take a proactive approach to preventing human hacking, beginning with establishing a comprehensive cybersecurity policy and employee training program.
Lazarus Alliance is proactive cybersecurity®. Call 1-888-896-7580 to discuss your organization’s cybersecurity needs and find out how we can help your organization adhere to cybersecurity regulations, maintain compliance, and secure your systems.



Related Posts