CJIS Compliance Audits & Certification | FBI CJIS Security Policy Experts - Lazarus Alliance. Call +1 (888) 896-7580 today.

The Federal Bureau of Investigation (FBI) established the Criminal Justice Information Services (CJIS) Security Policy to ensure the protection of sensitive criminal justice information (CJI) across law enforcement and related entities. Lazarus Alliance, an A2LA ISO/IEC 17020-accredited firm, collaborates directly with your organization to schedule and conduct CJIS compliance audits.
Our certified 3PAO Cybervisors™ assess your security controls against CJIS requirements, tailoring the evaluation to your organization’s specific operational needs. Upon successful demonstration of compliance, your organization will achieve CJIS Security Policy certification, ensuring robust protection of CJI.
Cybervisors™ are highly skilled cybersecurity professionals at Lazarus Alliance, certified to conduct audits and assessments, including CJIS compliance evaluations. They combine deep expertise in security frameworks like NIST SP 800-53 and CJIS Security Policy with practical experience to guide organizations through complex compliance processes. Using tools like the IT Audit Machine (ITAM), Cybervisors streamline evidence collection, risk management, and reporting, ensuring accurate, efficient results tailored to each client’s needs.
Criminal Justice Information Services (CJIS)
The FBI’s Criminal Justice Information Services (CJIS) Security Policy is a comprehensive set of standards designed to safeguard sensitive criminal justice information (CJI), including fingerprints, criminal histories, and background check data, accessed through FBI CJIS systems. Established under the FBI’s CJIS Division, the policy ensures the confidentiality, integrity, and availability of CJI for authorized users, such as law enforcement agencies, criminal justice organizations, and approved non-criminal justice entities (e.g., vendors conducting background checks).
The CJIS Security Policy outlines 13 policy areas derived from NIST SP 800-53, including:
- Access Control: Restricting system access to authorized users with proper authentication (e.g., multi-factor authentication).
- Awareness and Training: Mandating regular cybersecurity training for personnel handling CJI.
- Incident Response: Requiring plans to detect, report, and mitigate security incidents.
- Encryption: Ensuring data protection during transmission and storage using strong cryptographic standards.
- Physical Security: Safeguarding facilities and systems that store or process CJI.
- Personnel Security: Enforcing background checks and security clearances for individuals with access to CJI.
Compliance is mandatory for any organization accessing CJI, whether directly (e.g., police departments) or indirectly (e.g., third-party vendors). The policy requires triennial audits, typically conducted by accredited firms like Lazarus Alliance, to verify adherence to over 100 security controls. These audits assess technical, administrative, and physical safeguards, often using automated tools like the IT Audit Machine (ITAM) for efficient evidence collection and risk analysis.
Non-compliance can result in severe consequences, including loss of access to CJIS systems, fines, or legal repercussions, which could disrupt operations for agencies or vendors. The policy also evolves to address emerging threats, requiring organizations to stay updated on revisions. By enforcing rigorous standards, the CJIS Security Policy ensures the protection of sensitive data, fosters trust in the criminal justice ecosystem, and supports secure information sharing across federal, state, local, and tribal entities.
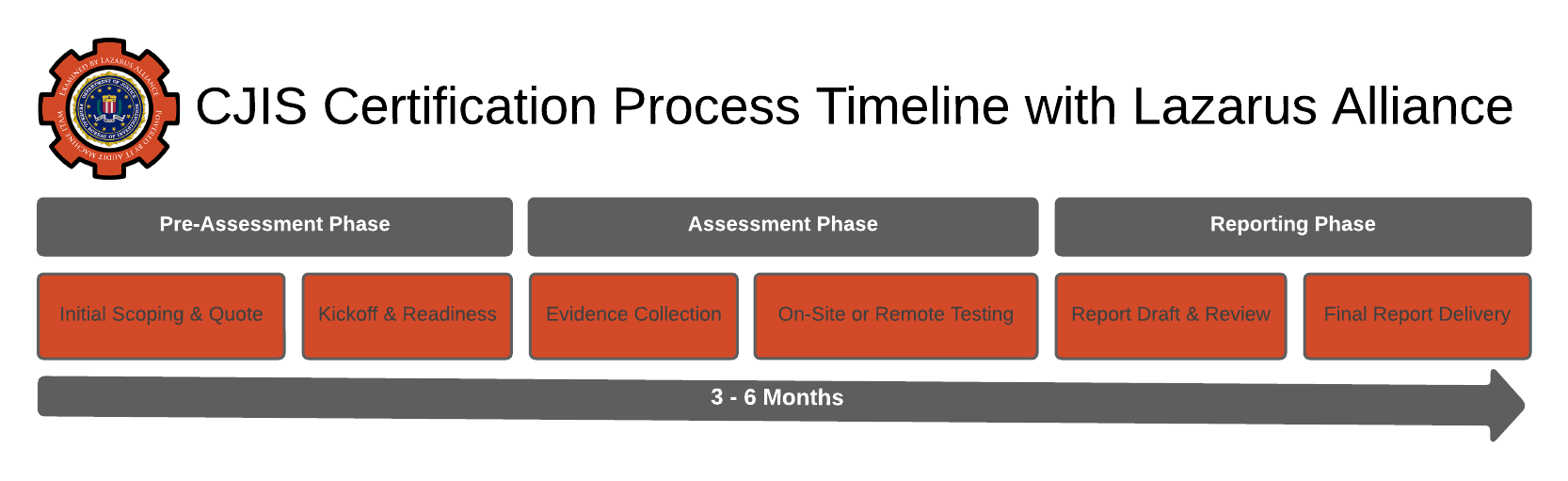
Basic CJIS Audit Timeline with Lazarus Alliance
Lazarus Alliance is an accredited cybersecurity and compliance firm specializing in FBI CJIS (Criminal Justice Information Services) Security Policy audits, particularly for private sector vendors, cloud providers, and organizations handling Criminal Justice Information (CJI). They use a proactive, tool-assisted approach (including our Continuum GRC IT Audit Machine, or ITAM) to make the process efficient, minimally disruptive, and focused on sustainable compliance. CJIS audits are required triennially (every three years) for ongoing access to CJI.
While exact timelines vary based on your organization's size, complexity, readiness, and any existing gaps, here's a typical step-by-step timeline and what to expect when working with Lazarus Alliance:
- Initial Engagement and Planning (1–4 weeks): You contact Lazarus Alliance for a consultation. They review your current environment, CJIS requirements, and scope the audit. This includes signing agreements and setting up access to their ITAM platform for automated evidence collection. Expect discussions on whether the audit will be remote, on-site, or hybrid.
- Stage 1: Gap Assessment/Readiness Review (2–8 weeks): Lazarus Alliance's certified Cybervisors™ conduct a thorough gap analysis against the CJIS Security Policy controls (mapped to NIST SP 800-53). Using ITAM, they automate much of the evidence gathering to identify deficiencies early. This phase determines your readiness and helps avoid surprises in the formal audit. You'll receive a detailed report highlighting gaps and recommended fixes.
- Remediation and Preparation (Variable: 1–6 months, depending on gaps): If gaps are found, you'll implement remediations (e.g., policy updates, technical controls, training). Lazarus Alliance provides guidance, Plans of Action and Milestones (POA&M), and ongoing support via ITAM for tracking progress. This is the most variable phase—well-prepared organizations may need little time, while others require more extensive work.
- Stage 2: Formal Audit and Evidence Collection (2–6 weeks): The official audit occurs (remote or on-site). Auditors verify compliance across technical, administrative, and physical controls using automated tools to minimize disruption. Interviews, document reviews, and system checks are conducted efficiently.
- Reporting, Verification, and Certification (2–4 weeks): You receive a comprehensive audit report. If compliant, Lazarus Alliance issues certification/documentation supporting your CJIS compliance (often required for CJIS Security Addendum agreements). Any minor remaining issues are verified quickly. Successful completion ensures continued CJI access.
- Ongoing Monitoring and Next Cycle: Post-audit, you get 24/7 access to the ITAM platform for continuous compliance monitoring. Lazarus Alliance emphasizes proactive maintenance to prepare for the next triennial audit.
Overall Timeline: For prepared organizations, the full process can take 3–6 months from start to certification. Organizations with significant gaps may need 6–12 months. Their automated, client-focused methodology (Proactive Cyber Security®) typically makes it faster and less burdensome than traditional audits.
For the most accurate timeline tailored to your situation, contact Lazarus Alliance directly at +1 (888) 896-7580 or via our website (lazarusalliance.com). We have extensive experience with clients like Cisco Systems, Scribbles Software, RestoreVault, VeriPic, and others, achieving CJIS compliance.

Frequently Asked Questions
What is the CJIS Security Policy?
The CJIS Security Policy is a set of standards established by the FBI's Criminal Justice Information Services (CJIS) Division to protect sensitive criminal justice information (CJI), such as fingerprints, criminal histories, and background check data. It covers 13 policy areas based on NIST SP 800-53, including access control, encryption, incident response, and physical security, ensuring the confidentiality, integrity, and availability of CJI for authorized users like law enforcement and vendors.
Who needs to comply with CJIS requirements?
Any organization that accesses CJI, either directly (e.g., police departments, criminal justice agencies) or indirectly (e.g., third-party vendors conducting background checks), must comply. This includes non-criminal justice entities approved by state CJIS Systems Agencies (CSAs), with mandatory triennial audits to verify adherence to over 100 security controls.
Why is CJIS compliance important for organizations?
Compliance safeguards sensitive data against breaches, ensures uninterrupted access to FBI CJIS systems, and avoids severe penalties like fines, legal actions, or loss of access. It also builds trust with partners, mitigates risks from emerging threats, and provides a competitive edge for vendors working with law enforcement.
| Impact Level | Baseline Controls (Approx.) | Key Use Cases | Reuse Scope |
|---|---|---|---|
| Low | ~125 NIST 800-53 Low controls | Public/low-sensitivity data (e.g., general websites) | SLED entities nationwide |
| Low+ | Enhanced Low (~150 controls) | Slightly elevated low-risk data (e.g., basic admin tools) | SLED entities nationwide |
| Moderate | ~325 NIST 800-53 Moderate controls + overlays | Confidential data (e.g., PII, financial records) | SLED entities nationwide |
| High | ~421 NIST 800-53 High controls + overlays | High-sensitivity data (e.g., critical infrastructure) | SLED entities nationwide |
| Core (Introduced May 2025) | 60 foundational Moderate controls (MITRE ATT&CK mapped) | Entry-level validation for progressing products | Broad pre-authorization access for SLED |
- Comprehensive Cybervisor™ Assessments using advanced software for low, moderate, and high-impact baselines.
- Ongoing proactive monitoring and 24/7 audit platform access.
What are the key consequences of non-compliance with CJIS?
Non-compliance can lead to immediate loss of access to CJIS systems, disrupting operations, financial fines, legal repercussions, and reputational damage. Organizations must stay updated on policy revisions (e.g., Version 5.9.2) to avoid these issues, as the policy evolves to address new cybersecurity threats.
What services does Lazarus Alliance provide for CJIS compliance?
As an A2LA ISO/IEC 17020-accredited firm (certification #3822.01), Lazarus Alliance offers gap assessments, official audits, and certification support using certified 3PAO Cybervisors™. They employ tools like the IT Audit Machine (ITAM) for evidence collection and risk management, following a Proactive Cyber Security® methodology to streamline the process and ensure sustainable compliance.
How does Lazarus Alliance conduct a CJIS audit?
Lazarus Alliance's Cybervisors™ perform tailored assessments against CJIS controls, collecting evidence via automated tools like ITAM to minimize disruption. The process includes gap analysis, on-site or remote audits, remediation planning through Plans of Action and Milestones (POA&M), and verification, leading to official compliance certification upon successful demonstration.
What tools and methodologies does Lazarus Alliance use for CJIS?
They utilize the IT Audit Machine (ITAM) for automated evidence gathering, risk analysis, and reporting; the Policy Machine for developing security standards; and a proven project plan based on NIST SP 800-53 and Proactive Cyber Security®. These tools reduce audit time and support ongoing monitoring for long-term compliance.
What is the process to achieve and maintain CJIS compliance?
The process involves: (1) understanding requirements and conducting a gap assessment; (2) implementing controls like multi-factor authentication, encryption, and training; (3) engaging accredited auditors for evidence review; (4) remediating issues via POA&M; (5) achieving certification; and (6) maintaining through regular internal reviews, updates to policy changes, and triennial re-audits.
Credentials You Can Count On
American Association for Laboratory Accreditation (A2LA) ISO/IEC 17020 accredited certification number 3822.01.

Talk with one of our experts
Our Lazarus Alliance Cybervisor™ teams have experience performing thousands of assessments for organizations providing services to clients around the world.
We're here to answer any questions you may have.


Benefits of CJIS Compliance
CJIS compliance, mandated by the FBI’s Criminal Justice Information Services Security Policy, offers several key benefits for organizations handling criminal justice information (CJI):
- Enhanced Data Security: Compliance ensures robust safeguards for sensitive CJI, reducing the risk of data breaches, unauthorized access, or cyber threats.
- Access to Critical Systems: Compliant organizations gain authorized access to FBI CJIS systems, enabling seamless interaction with criminal justice databases essential for law enforcement and background check operations.
- Legal and Regulatory Adherence: Meeting CJIS requirements avoids penalties, legal liabilities, or loss of access to CJI, ensuring uninterrupted operations for agencies and vendors.
- Improved Trust and Reputation: Demonstrating compliance signals a commitment to security, building trust with partners, clients, and stakeholders in the criminal justice ecosystem.
- Risk Mitigation: Regular audits and controls mandated by CJIS identify vulnerabilities, enabling proactive risk management and a stronger cybersecurity posture.
- Operational Efficiency: Streamlined processes, often supported by tools like Continuum GRC’s ITAM, reduce the complexity and time required to maintain compliance.
- Competitive Advantage: For vendors and non-criminal justice entities, CJIS compliance can differentiate your organization, opening opportunities to work with law enforcement and government agencies.
By achieving and maintaining CJIS compliance, organizations protect sensitive data, ensure operational continuity, and strengthen their credibility in handling CJI.
CJIS Certification Process
The CJIS certification process, governed by the FBI’s Criminal Justice Information Services (CJIS) Security Policy, ensures organizations handling criminal justice information (CJI) meet stringent security standards. While there is no formal "CJIS certification" issued as a standalone credential, compliance with the CJIS Security Policy is verified through a structured assessment and audit process. Below is a detailed overview of the steps involved:
- Understand CJIS Requirements:
- Organizations must familiarize themselves with the CJIS Security Policy (Version 6 as of the latest updates), which outlines 13 policy areas, including access control, encryption, incident response, personnel security, and physical security, mapped to NIST SP 800-53 controls.
- Determine the scope of CJI access, whether direct (e.g., law enforcement agencies) or indirect (e.g., vendors or non-criminal justice agencies like those processing background checks).
- Conduct a Gap Assessment:
- Perform an internal review to identify gaps between current security practices and CJIS requirements. This includes evaluating technical controls (e.g., firewalls, encryption), administrative policies (e.g., training, incident response plans), and physical safeguards (e.g., secure facilities).
- Many organizations engage accredited firms like Lazarus Alliance to conduct a preliminary assessment, leveraging tools like the Continuum GRC IT Audit Machine (ITAM) for automated evidence collection and gap analysis.
- Implement Security Controls:
- Address identified gaps by implementing required controls, such as:
- Multi-factor authentication (MFA) for system access.
- Encryption for data in transit and at rest (e.g., FIPS 140-2 compliant algorithms).
- Background checks for personnel with CJI access.
- Security awareness training for all staff.
- Develop or update policies and procedures to align with CJIS standards, including incident response plans and access control protocols.
- Address identified gaps by implementing required controls, such as:
- Engage an Accredited Auditor:
- For organizations subject to triennial audits (typically state, local, or tribal agencies with direct CJIS access), hire an accredited firm, such as Lazarus Alliance, to conduct the official compliance audit.
- Non-criminal justice agencies (e.g., vendors) may require assessments as part of their authorization to access CJI, often coordinated through a state CJIS Systems Agency (CSA) or contracting authority.
- Audit and Evidence Collection:
- The audit involves a comprehensive review of the organization’s security posture, including documentation, system configurations, and physical security measures.
- Auditors collect evidence to verify compliance with CJIS controls, often using automated tools to streamline the process and ensure accuracy.
- For example, Lazarus Alliance’s Cybervisors™ use ITAM to gather and analyze evidence, reducing audit time and minimizing disruption.
- Address Findings and Remediation:
- If non-compliance issues are identified, the organization receives a report detailing deficiencies and recommended corrective actions.
- Develop a Plan of Action and Milestones (POA&M) to address findings within a specified timeframe, typically coordinated with the state CSA or FBI CJIS auditors.
- Re-assessments may be required to confirm remediation.
- Receive Compliance Verification:
- Upon successful audit and remediation, the organization is deemed compliant with the CJIS Security Policy. For agencies, this is documented through the state CSA or FBI CJIS Division. For vendors, compliance is often tied to specific contracts or agreements.
- Compliance status allows continued access to CJIS systems and data, subject to ongoing monitoring and triennial re-audits.
- Maintain Ongoing Compliance:
- Organizations must continuously monitor and maintain compliance through regular training, system updates, and incident reporting.
- Stay informed about CJIS Security Policy updates, as requirements evolve to address new cyber threats.
- Conduct internal reviews or engage third-party firms periodically to ensure readiness for triennial audits.
By working with experienced auditors like Lazarus Alliance, organizations can streamline the process, leveraging expertise and tools to achieve and maintain CJIS compliance efficiently.

Buyer Beware!
The Criminal Justice Information Services (CJIS) is based on the NIST SP 800-53 compliance framework, which is complex and extensive in scope. Very few providers out there are actually qualified to properly conduct a Criminal Justice Information Services (CJIS) assessment.
Lazarus Alliance is one of the few accredited Third Party Assessment Organizations (3PAO) by the American Association for Laboratory Accreditation (A2LA) ISO/IEC 17020 certification number 3822.01. We are also a recognized Government Records & Access Management Program (GovRAMP - StateRAMP) accredited Third Party Assessment Organization (3PAO).
Any Criminal Justice Information Services (CJIS) that cannot validate that they are also an accredited Third Party Assessment Organization (3PAO) like Lazarus Alliance will not be able to get your organization fully authorized under the new program.
For CJIS services that reduce costs and leverage the number one ranked CJIS audit software and ONLY GovRAMP | FedRAMP Authorized assessment platform, call +1 (888) 896-7580 to get started. — Michael Peters, CEO & Founder
