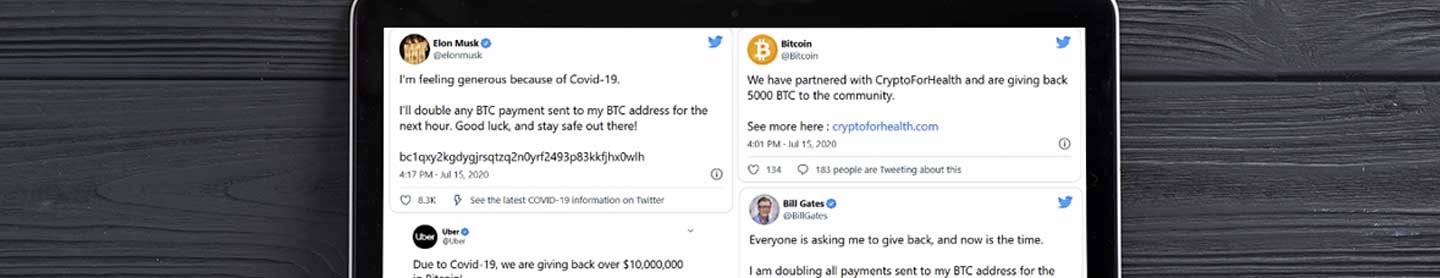
On July 16, the social media platform Twitter experienced one if not the most significant, security breaches in its history when cybercriminals hacked into major public figures’ verified accounts and convinced users worldwide to transfer them nearly $120,000 in bitcoin. What can other organizations learn from this Twitter hack?
Key Cyber Security Lessons from the 2020 Twitter Hack