Vulnerability Scanning, Penetration Testing, and Red Team Support Services from Lazarus Alliance. Call +1 (888) 896-7580 today!
Table of Contents
Toggle
Today's cyber attackers are more advanced than at any time in modern history. With the growth of worldwide hacking groups and state-sponsored attacks, no industry sector is immune from attack. It is more important than ever to remain vigilant and to ensure vulnerability management and penetration testing resources are included in your overall risk management plans and execution.
Incident response has become an important component of information technology (IT) programs. Because performing incident response effectively is a complex undertaking, establishing a successful incident response capability requires substantial planning and resources.
Lazarus Alliance Red Team exercises extend the objectives of penetration testing by examining the security and privacy posture of organizations and the capability to implement effective cyber defenses. Lazarus Alliance Red Team exercises simulate attempts by adversaries to compromise mission and business functions and provide a comprehensive assessment of the security and privacy posture of systems and organizations. Such attempts may include technology-based attacks and social engineering-based attacks.
Lazarus Alliance Red Team exercises are conducted by Lazarus Alliance penetration testing teams with knowledge of and experience with current adversarial tactics, techniques, procedures, and tools.
Lazarus Alliance Service Capabilities Include:
- Accredited to NIST 800-115
- Red Team exercises
- Static Code Analysis
- Dynamic Code Analysis
- Authenticated Vulnerability Testing
- Unauthenticated Vulnerability Testing
- Authenticated Penetration Testing
- Unauthenticated Penetration Testing
- SCAP Benchmark Testing
- Physical Security Testing
- Wireless Security Testing
- Social Engineering or Human Hacking
- Phishing Testing
While penetration testing may be primarily laboratory-based testing in coordination with the Lazarus Alliance NVLAP Laboratory during Common Criteria testing or part of FedRAMP, StateRAMP, and NIST 800-53 3PAO testing, organizations can use red team exercises to provide more comprehensive assessments that reflect real-world conditions.
The results from red team exercises can be used by organizations to improve security and privacy awareness and training and to assess control effectiveness.
A Lazarus Alliance Red Team assessment is a comprehensive security testing technique that involves simulating real-world cyberattacks on an organization's systems, networks, and infrastructure. The Lazarus Alliance Red Team, comprised of skilled Cybervisor© professionals, acts as the adversary, attempting to breach the organization's defenses using tactics, techniques, and procedures (TTPs) similar to those employed by malicious actors.
The primary objective of a Lazarus Alliance Red Team assessment is to identify vulnerabilities, weaknesses, and gaps in an organization's security posture that could be exploited by attackers. By conducting simulated attacks from an external or internal threat perspective, the Lazarus Alliance Red Team helps organizations enhance their security resilience, incident response capabilities, and overall cybersecurity readiness.
The following illustration depicts the organized rigor involved with our incident response service lifecycle.
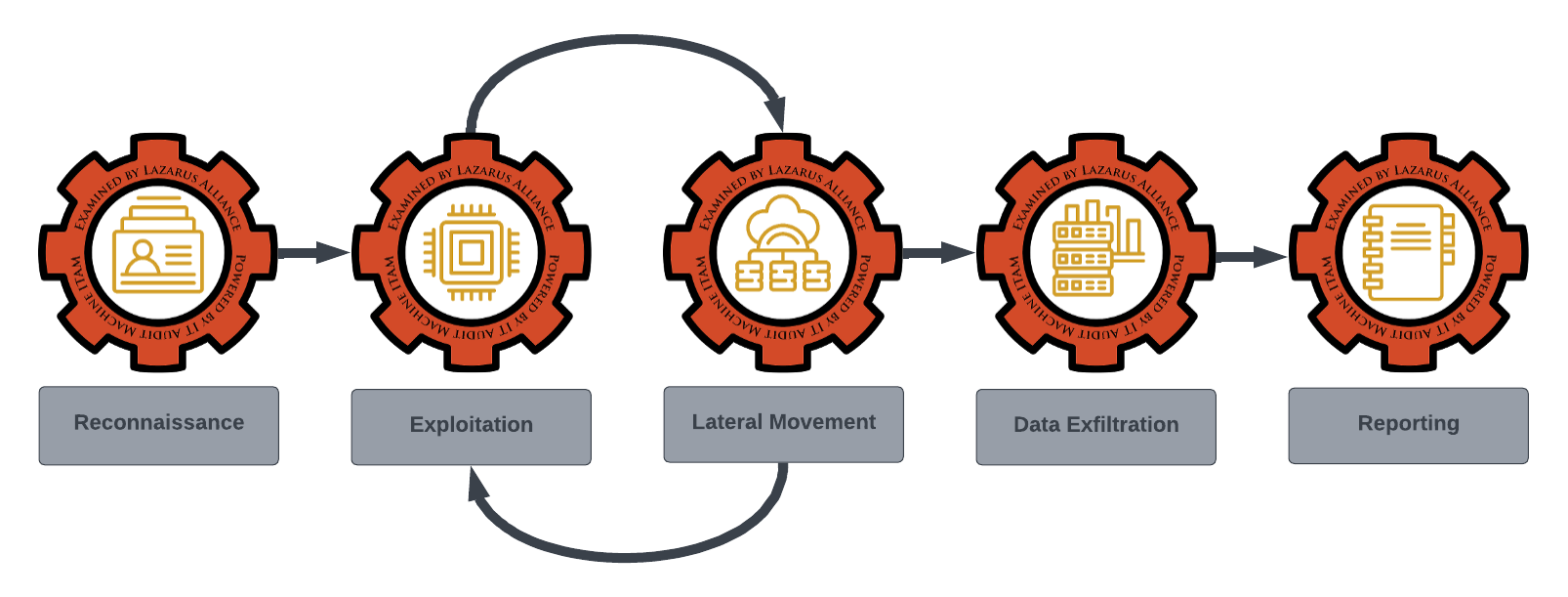
Lazarus Alliance utilizes the NIST 800-61 Computer Security Incident Handling Guide as the foundation for our well-managed incident response and Lazarus Alliance Red Team services.
Key components of a Lazarus Alliance Red Team assessment include:

Reconnaissance
Gathering information about the target organization to identify potential entry points and vulnerabilities.
The Lazarus Alliance Red Team conducts reconnaissance activities to gather information about the target organization, its systems, networks, and security controls. This may involve passive information gathering through open-source intelligence (OSINT) and active scanning to identify potential attack vectors.
Lazarus Alliance Red Team members may attempt social engineering techniques, such as phishing emails or phone calls, to manipulate employees into revealing confidential information or granting unauthorized access to systems.
The Lazarus Alliance Red Team identifies and exploits vulnerabilities in the organization's infrastructure, applications, and services to gain unauthorized access or escalate privileges.

Exploitation
Attempting to exploit identified vulnerabilities to gain unauthorized access to systems or sensitive data.
Using the information gathered during reconnaissance and vulnerability analysis, the Lazarus Alliance Red Team attempts to exploit weaknesses in the organization's defenses to gain access to sensitive data or systems.

Lateral Movement
Moving laterally within the network to escalate privileges and access additional resources.
Once initial access is achieved, the Lazarus Alliance Red Team moves laterally within the network to explore and exploit additional systems, mimicking the tactics of a sophisticated attacker.
Lazarus Alliance Red Team members attempt to escalate privileges to gain higher levels of access within the network, potentially reaching critical systems or sensitive data repositories.

Data Exfiltration
Attempting to extract sensitive data or information from the organization's systems without detection.
The Lazarus Alliance Red Team simulates the extraction of sensitive data from the organization's systems without detection, demonstrating the potential impact of a successful cyberattack.

Reporting
Providing a detailed report of the assessment findings, including vulnerabilities exploited, recommendations for remediation, and potential improvements to security defenses.
Following the exercise, the Lazarus Alliance Red Team compiles a detailed report outlining the findings, vulnerabilities exploited, potential risks, and recommendations for enhancing the organization's security posture.

Frequently Asked Questions
Vulnerability scanning identifies potential weaknesses in systems through automated tools, while penetration testing (pen testing) simulates real-world attacks by ethical hackers to exploit those weaknesses and assess impact. Lazarus Alliance offers both, including authenticated and unauthenticated testing, to provide actionable insights into your security posture. Vulnerability scanning remains largely automated and detection-focused, identifying potential issues without exploitation. Penetration testing actively exploits vulnerabilities, tests defenses against sophisticated tactics (now including AI agents and autonomous attacks), and assesses impact. In 2026's threat landscape, Lazarus Alliance's manual and hybrid approaches go beyond basic scans to uncover exploitable gaps that automated tools alone miss. Lazarus Alliance provides comprehensive, NIST-accredited penetration testing, including authenticated/unauthenticated assessments, web/network/app testing, static/dynamic analysis, wireless/physical security, social engineering, phishing, and full Red Team simulations. With 2026's rise in AI-powered attacks, our services now emphasize testing resilience against agentic AI threats, shadow AI risks, and evolving adversary TTPs. Yes, Lazarus Alliance is accredited to NIST Special Publication 800-115, the technical guide for information security testing and assessment. Our Cybervisor© professionals deliver ethical, controlled testing aligned with industry best practices, including support for FedRAMP, StateRAMP, and NIST 800-53 compliance. Timelines depend on scope (e.g., network scale, app complexity, Red Team depth against AI tactics), but our efficient process—reconnaissance through exploitation, reporting, and remediation guidance—adapts to 2026's faster threat cycles. Contact us at +1 (888) 896-7580 for a tailored scoping call that factors in current AI and quantum-related considerations. Yes—Lazarus Alliance remains accredited to NIST Special Publication 800-115, with Cybervisor© experts delivering ethical testing that aligns with FedRAMP, StateRAMP, NIST 800-53, and emerging 2026 priorities like AI governance, post-quantum cryptography readiness, and regulatory volatility. We help clients stay ahead in an era of accelerating AI adoption and geopolitical cyber risks. As a 26+-year leader in Proactive Cyber Security®, Lazarus Alliance combines accredited human-led testing with awareness of 2026 trends—such as AI agent proliferation, adversarial AI, and the shift to continuous/automated testing—to deliver superior insights. Our services identify real exploitable risks, support compliance amid global regulatory shifts, and fortify defenses against the year's most pervasive threats. Penetration testing validates controls for FedRAMP, StateRAMP, NIST 800-53, and 2026's evolving mandates around AI risk management, cyber resilience, and post-quantum readiness. As an experienced 3PAO partner, Lazarus Alliance conducts compliant, privileged testing to demonstrate mitigation of real-world risks—including AI-driven threats—in authorization packages. What is vulnerability scanning and penetration testing?
What is Red Team testing and how does it differ from standard penetration testing?
What does Lazarus Alliance’s penetration testing service include in 2026?
Is Lazarus Alliance accredited for penetration testing?
How long does a Lazarus Alliance penetration test or Red Team assessment take?
Is Lazarus Alliance accredited and prepared for 2026 cybersecurity challenges?
Why choose Lazarus Alliance for vulnerability and penetration testing in 2026?
How does penetration testing support compliance like FedRAMP, NIST, or emerging 2026 regulations?
By performing these activities in a controlled and ethical manner, Lazarus Alliance Red Teams help organizations identify weaknesses, improve incident response capabilities, and strengthen overall cybersecurity defenses against real-world threats.

Credentials You Can Count On
American Association for Laboratory Accreditation (A2LA) ISO/IEC 17020 accredited certification number 3822.01.

Talk with one of our experts
Our Lazarus Alliance Cybervisor™ teams have experience performing thousands of assessments for organisations providing services to clients around the world.
We're here to answer any questions you may have.
