Risk Assessment and Risk Management; we are ready when you are! Call +1 (888) 896-7580 today.
Table of Contents
Toggle
Risk management is so fundamentally important to business survival. Organizations all around the world are suffering through cyber-attacks; some unsuccessfully. Espionage and Hacktivism is on the rise.
As if that were not enough, increased regulatory demands, pressure from top management for faster and better business information, and advances in risk management by top-tier competitors are prompting smart companies to transform their risk functions.
Lazarus Alliance is the Solution
Defending against today’s cyber threat landscape requires a proactive, real-time approach to managing risk. In this fast evolving environment, the challenge is for private and public sector organizations to manage risk in the purest sense – by making informed, predictive risk-based decisions, rather than implementing controls in an ad hoc or reactive manner.
Want to learn more?

Preeminent Qualifications
Retain the team that is comprised of internationally recognized information security, privacy, risk management and governance professionals.
Hire the best-of-the-best! Our team created the leading Integrated Risk Management (IRM) and Governance, Risk and Compliance (GRC) assessment software tools.
We provide comprehensive services that either augment your staff or completely lead bringing the exact talent to bear rapidly which leads to your success.

Integrated Risk Management
Leveraging Continuum GRC's ITAM IRM GRC assessment platform, we provide the #1 ranked assessment software platform to our clients supporting:
- Integrated Risk Management
- Digital Risk Management
- Vendor Management
- Business Continuity Management
- Audit Management
- Corporate and Compliance Oversight

Enterprise Data Concentric Perspectives
Our IT security assessments gauge the “health” of our clients’ technology and business operational environments to determine if they are “doing the right things” with their security and integrated risk management programs.
Our assessments are data concentric meaning we start with the most important business asset which revolves around data.

Comprehensive Support
Leaving no stone unturned, our integrated risk management program services cover all facets of your risk management program offering services such as:
- Vendor Risk Assessments
- Vendor Management
- Internal Risk Assessment
- Integrated Risk Management Programming
- Software Development Life Cycle Vulnerability Assessment and Penetration Testing Services
- Static Code Analysis
- Digital Risk Management
- NIST 800-53, NIST 800-30, NIST 800-37, ISO 27005, and ISO 27001 Corporate Compliance Management Programs
- Business Continuity Management
Setting the Standards
Be Proactive Not Reactive
Identify and fix risks proactively with Lazarus Alliance giving you and your customers independent third-party assurances.
The Choice Is Yours
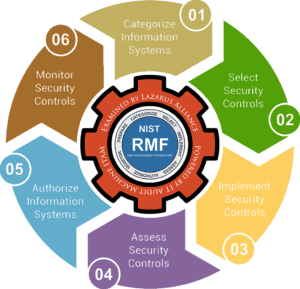
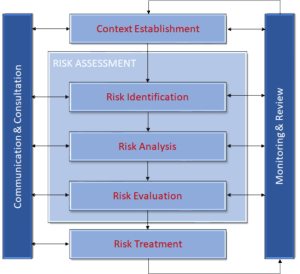
These two illustrations depict the normal systematic risk assessment and management life cycle. Lazarus Alliance’s Cybervisors® will help guide you through the complexities of the risk management process regardless of whether your organization requires or prefers the NIST Risk Management Framework Life Cycle or the ISO Risk Management Framework Life Cycle.
NIST Risk Management Framework Life Cycle

ISO Risk Management Framework Life Cycle
We understand the key issues you are facing.
- 83% of organizations have no formal cyber security plan. (Source: National Cyber Security Alliance)
- Thousands of breaches have occurred over the last 12 months. (Source: US Secret Service)
- 48% of breaches were caused by insiders which means employees and trusted business partners. (Source: US Secret Service)
- 96% of breaches were avoidable through simple or intermediate controls. (Source: US Secret Service)
- 67% of security professionals are unqualified to do the job. (HP Cyber-security study)
Our core risk management activities include:
- Business Alignment: Initially, core business assets in the form of intellectual property, databases and other sensitive company data is identified, prioritized and value defined from a business value perspective.
- Framework Alignment: Depending on whether your business is a government agency or private sector business, there are common risk management frameworks used that provide consistent results that are sustainable.
- Risk Identification: What is the likelihood that your core business assets might suffer a breach or loss in some way that adversely affects your business? We identify the risks and their likelihood giving you a more accurate picture on protecting those code business assets.
- Threat Analysis: Are the threats facing your core business assets forces or nature or forces of human nature? The point is we identify the risks to your core business assets.
- Risk Elimination: Now that we have identified the risks to your code business assets, we work together to formulate a strategy for eliminating risks to your business.
- Vigilance: It’s not the end of the road following the completion of a proper risk assessment. There are controls that need monitoring, testing and tuning to ensure that your risk mitigation strategy is working.
- Incident Response: Even with the best preparations come the occasion where situations beyond control occur. The illusion is that they are beyond our control. Incident response preparations are an essential component to your risk management strategy.
Small Business – Big Business: Does it matter?
- Represent 99.7 percent of all employer firms.
- Employ half of all private sector employees.
- 60% are out of business 6 months post-breach.
- Pay 44 percent of total U.S. private payroll.
- Generated 65 percent of net new jobs over the past 17 years.
- Made up 97.5 percent of all identified exporters.
- Produce 13 times more patents per employee than large patenting firms.
