NIST RMF & NIST 800-37 Compliance Audits | Risk Management Experts - Lazarus Alliance. Call +1 (888) 896-7580 today!


NIST SP 800-37 is a key publication from the National Institute of Standards and Technology (NIST) titled Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy (current revision: Revision 2, published December 2018).
It provides guidelines for implementing the Risk Management Framework (RMF), a structured, disciplined, and flexible process for effectively managing cybersecurity and privacy risks throughout the entire system life cycle.
The RMF is mandatory for federal agencies under FISMA (Federal Information Security Modernization Act) and OMB Circular A-130, but it is widely adopted by other organizations (including private sector and contractors) as a best practice for risk-based security and privacy management.
NIST Special Publication 800-53, titled "Security and Privacy Controls for Information Systems and Organizations," is a comprehensive framework developed by the National Institute of Standards and Technology (NIST) to provide guidelines for securing federal information systems and organizations. It outlines a catalog of security and privacy controls to protect against a wide range of threats, ensure compliance with federal regulations, and safeguard sensitive data.
Lazarus Alliance, a certified Third-Party Assessment Organization (3PAO), will collaborate directly with your organization to schedule your NIST RMF and NIST 800-37 assessments. Our certified 3PAO assessors will assist in determining the appropriate impact level based on your company’s unique business and government requirements.
NIST RMF & NIST 800-37
- Integrates security and privacy considerations into a single holistic framework.
- Emphasizes risk management at organizational, mission/business process, and system levels.
- Promotes continuous monitoring and near real-time risk management rather than one-time assessments.
- Incorporates supply chain risk management and prepares organizations through foundational activities.
The Seven Steps of the RMF
- Prepare: Establish essential risk management activities and organizational context (new in Rev. 2 to improve execution success).
- Categorize: Classify the system and the information it processes, stores, and transmits based on potential impact.
- Select: Choose an initial set of security and privacy controls (typically from NIST SP 800-53) tailored to the system's risk.
- Implement: Put the selected controls into place and document how they are deployed.
- Assess: Evaluate whether the controls are implemented correctly, operating as intended, and producing the desired outcomes.
- Authorize: Senior leadership makes a risk-based decision to authorize the system (or common controls) to operate.
- Monitor: Continuously track control effectiveness, risks, and changes to maintain authorization and respond to new threats.
This framework helps organizations align security and privacy with mission/business objectives, make informed risk decisions, and maintain ongoing authorization through continuous monitoring. The full document is available on the NIST website: https://csrc.nist.gov/pubs/sp/800/37/r2/final.
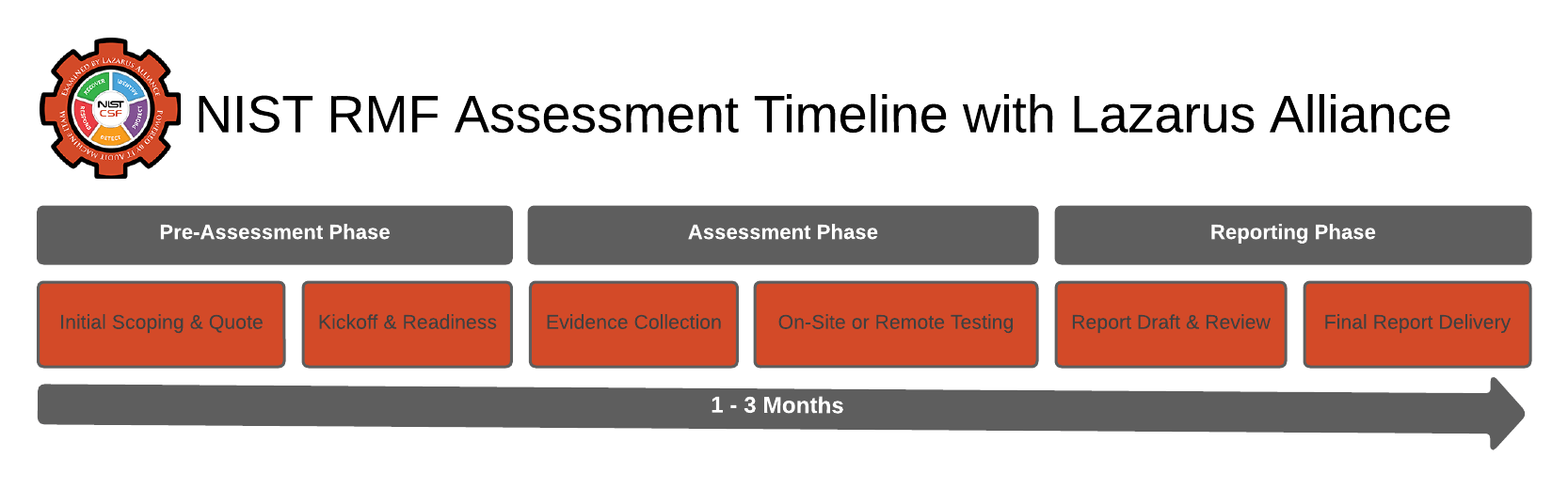
Basic NIST RMF & NIST 800-37 Audit Timeline with Lazarus Alliance
The typical timeline for conducting a NIST Risk Management Framework (RMF) process is defined in NIST SP 800-37. Lazarus Alliance, a certified Third-Party Assessment Organization (3PAO), provides these services for federal, DoD, and related systems requiring NIST 800-53 control assessments to support Authorization to Operate (ATO) decisions.
Lazarus Alliance uses its proprietary IT Audit Machine™ platform and Critical Path Methodology to accelerate assessments by up to 46% compared to traditional methods. The SCA-V phase (primarily the Assess step in RMF) focuses on evaluating implemented security and privacy controls.
Typical Duration: 6–12 weeks from project kickoff to delivery of the final Security Assessment Report (SAR).
- Fastest realistic timeline (well-prepared client with pre-loaded evidence and full automation): ~6–8 weeks.
- Average for most organizations: 8–10 weeks (includes minor remediation).
- Longer timelines: 10–12+ weeks (more complex systems, larger scope, or significant gaps/remediation).
Key phases:
- Pre-Engagement & Planning
- NDA/SOW signing, kickoff call, document upload (e.g., SSP, boundary diagram, prior SAR/POA&Ms) to the platform.
- Finalize Security Assessment Plan (SAP) with automated scoping. Duration: ~1 week (accelerated by 24/7 platform access). Deliverables: Signed SOW, approved SAP, Rules of Engagement, baseline readiness report.
- Evidence Collection & Preparation Support
- Automated evidence upload/validation, gap analysis for missing items. Duration: 1–2 weeks (often parallel with Phase 1; tool-driven).
- Assessment Execution
- Document reviews, interviews, automated/manual testing (vulnerability scans, configuration checks, NIST 800-53A procedures). Duration: 2–4 weeks (core fieldwork; 46% faster due to tools). Deliverables: Weekly status reports, preliminary findings log.
- Subsequent Phases (implied in the overall 6–12 weeks)
- Findings validation, remediation support (if needed), final SAR/POA&M development, and reporting.
- Ongoing continuous monitoring follows for ATO maintenance.
Frequency: Full assessments typically occur every 3 years for ATO renewal, with continuous monitoring required in between. RMF itself is an ongoing lifecycle, not a one-time audit.
This timeline applies specifically to Lazarus Alliance's efficient approach using automation. Actual duration varies based on system complexity, preparation level, scope (e.g., Low/Moderate/High impact), and remediation needs.

Frequently Asked Questions
Yes. Early gap analysis identifies issues, and they provide remediation support, control implementation guidance, and readiness reporting. In 2026, this includes help with AI-related controls, supply chain risk integration, and alignment to recent NIST publications (e.g., AI overlays, enhanced patching). Their platform flags gaps quickly for proactive resolution. NIST SP 800-37 (Revision 2) provides the guidelines for the Risk Management Framework (RMF), a structured, risk-based process for managing cybersecurity and privacy risks throughout the system life cycle. It includes seven steps: Prepare, Categorize, Select, Implement, Assess, Authorize, and Monitor. Lazarus Alliance helps organizations implement and audit against this framework to achieve and maintain compliance. These services are mandatory for U.S. federal agencies under FISMA and OMB Circular A-130, and are widely required for DoD contractors, systems seeking Authorization to Operate (ATO), FedRAMP-aligned cloud services, and private-sector organizations handling sensitive data or pursuing best-practice risk management. Lazarus Alliance, as a certified 3PAO, supports federal, DoD, contractors, and critical infrastructure clients. Contact Lazarus Alliance at +1 (888) 896-7580 or via the website form. They'll schedule a consultation to scope your needs, address 2026-specific risks (e.g., AI threats), sign NDA/SOW as required, and launch with a customized Security Assessment Plan (SAP). Their team guides you through preparation for efficient, audit-ready outcomes. An accredited 3PAO provides objective expertise, experience with DDTC expectations, and often cross-compliance insights (e.g., with related frameworks like NIST or CMMC). Lazarus Alliance, known for its work in federal compliance areas, delivers thorough, defensible reports that help demonstrate proactive compliance to primes, customers, or regulators, while identifying practical remediation steps. Lazarus Alliance uses the IT Audit Machine™ platform and Critical Path Methodology for 24/7 access, automated evidence upload/validation, scoping, gap analysis, and testing. This tool-driven process reduces manual effort, enables parallel phases (e.g., evidence collection during planning), and delivers faster, higher-quality results compared to traditional assessments. Typical timelines remain 6–12 weeks from kickoff to final SAR. Optimized clients using full automation achieve 6–8 weeks, with averages at 8–10 weeks. Complex systems or remediation needs may extend to 10–12+ weeks. Lazarus Alliance's IT Audit Machine™ and Critical Path Methodology continue to accelerate processes by up to 46%, especially valuable in 2026's fast-evolving threat environment requiring rapid authorization. Yes — Lazarus Alliance is an A2LA-accredited Third-Party Assessment Organization (3PAO) under ISO/IEC 17020 (certification #3822.01). Their Cybervisor™ teams have extensive experience conducting thousands of assessments, ensuring credible, audit-ready results accepted by authorizing officials. Can Lazarus Alliance assist if my organization has gaps or emerging 2026 risks?
What is NIST SP 800-37 and the Risk Management Framework (RMF)?
Who needs NIST 800-37 / RMF audit services?
How do I start a NIST 800-37 / RMF audit with Lazarus Alliance in 2026?
What are the benefits of using an accredited 3PAO like Lazarus Alliance for an ITAR assessment in 2026?
What makes Lazarus Alliance’s approach faster and more efficient?
How long does a NIST 800-37 / RMF assessment take with Lazarus Alliance in 2026?
Is Lazarus Alliance accredited or certified to perform these audits?
Credentials You Can Count On
American Association for Laboratory Accreditation (A2LA) ISO/IEC 17020 accredited certification number 3822.01.

Talk with one of our experts
Our Lazarus Alliance Cybervisor™ teams have experience performing thousands of assessments for organizations providing services to clients around the world.
We're here to answer any questions you may have.

Benefits of NIST RMF & 800-37 Compliance
NIST SP 800-37 (Revision 2) defines the Risk Management Framework (RMF), a structured, risk-based process for managing cybersecurity and privacy risks across the system life cycle. Compliance with the RMF (mandatory for U.S. federal agencies under FISMA and widely adopted in the private sector, DoD, contractors, and critical infrastructure) delivers significant advantages beyond basic regulatory adherence.
Here are the key benefits:
- Enhanced Security Posture and Resilience: Integrates security and privacy early into system development and operations, leading to stronger defenses, better threat detection, faster incident response, and reduced vulnerability to cyberattacks.
- Improved Risk Visibility and Informed Decision-Making: Provides clear, organization-wide visibility into risks at multiple levels (organizational, mission/business process, and system). Enables senior leaders to prioritize resources, make cost-effective risk decisions, and align security with business/mission objectives.
- Regulatory and Contractual Compliance: Helps meet mandatory requirements (e.g., FISMA for federal systems) and aligns with related standards like FedRAMP, DoD RMF, HIPAA, PCI DSS, ISO 27001, and others. Supports achieving and maintaining Authority to Operate (ATO), continuous ATO (cATO), or certifications.
- Customization and Scalability: Flexible and tailorable to any organization size, sector, or system impact level (Low, Moderate, High). Allows tailoring of controls from NIST SP 800-53 to fit specific needs, environments, and risk tolerances.
- Efficiency, Cost-Effectiveness, and Resource Optimization: Promotes near real-time risk management through continuous monitoring instead of periodic assessments. Reduces redundancy, streamlines processes (especially with automation), and focuses efforts on high-priority risks, leading to lower long-term costs.
- Integration of Security and Privacy into the System Life Cycle: Embeds risk management throughout design, development, acquisition, operation, and disposal phases. Incorporates supply chain risk management and prepares organizations for emerging threats.
- Better Stakeholder Communication and Trust: Establishes a common language and structured methodology for discussing risks. Builds confidence with customers, partners, regulators, and executives by demonstrating proactive, risk-based security practices.
- Support for Continuous Improvement and Adaptability: Encourages ongoing monitoring and authorization, enabling organizations to adapt quickly to new threats, changes, or technologies while maintaining authorization.
Overall, adopting the RMF via NIST SP 800-37 shifts organizations from reactive compliance checklists to a proactive, holistic risk management approach. This not only reduces cyber risk exposure but also supports business continuity, innovation, and competitive advantage.
For the official source, see the full document: NIST SP 800-37 Rev. 2. Many organizations including those working with Lazarus Alliance, find these benefits accelerate ATO processes and improve audit outcomes when implemented effectively.

Lazarus Alliance utilizes the Continuum GRC IT Audit Machine, Security Trifecta methodology, and Policy Machine to deliver internationally recognized “Best Practices” for establishing organizational security standards and controls. These support compliance with NIST RMF & NIST 800-37-based audit certifications and assessments.
